Graduate Aptitude Test in Engineering 2017
Question Paper Name: Computer Science and Information Technology 11th Feb 2017 Session 2
Subject Name: Computer Science and Information Technology
Duration : 180
Total Marks: 100
1. Consider the set X={a, b,c,d,e} under the partial ordering
R={(a,a),(a,b),(a,c),(a,d),(a,e),(b,b),(b,c),(b,e),(c,c),(c,e),(d,d),(d,e),(e,e)}.
The Hasse diagram of the partial order (X, R) is shown below.
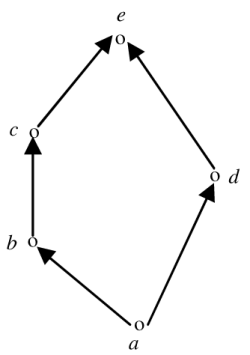
The minimum number of ordered pairs that need to be added to R to make (X, R) a lattice is ________.
Ans: (0)
2. Which of the following statements about parser is/are CORRECT?
I. Canonical LR is more powerful than SLR.
II. SLR is more powerful than LALR
III. SLR is more powerful than Canonical LR.
(A) I only
(B) II only
(C) III only
(D) II and III only
Ans: (A)
3. Match the following:
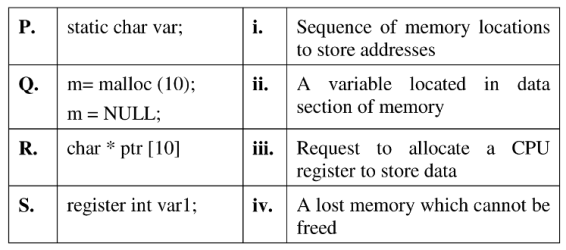
(A) P-(ii), Q-(iv), R-(i), S-(iii)
(B) P-(ii), Q-(i), R-(iv), S-(iii)
(C) P-(ii), Q-(iv), R-(iii), S-(i)
(D) P-(iii), Q-(iv), R-(i), S-(ii)
Ans: (A)
4. Let L1, L2 be any two context free languages and R be any regular language. Then which of the following is/are CORRECT ?
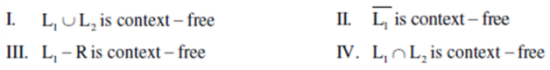
(A) I, II and IV only
(B) I and III only
(C) II and IV only
(D) I only
Ans: (B)
5. G is undirected graph with n vertices and 25 edges such that each vertex of G has degree at least 3. Then the maximum possible value of n is ___________.
Ans: (16)
6. Let p, q, r denote the statements “It is raining ,“ It is cold”, and “ It is pleasant,” respectively. Then the statement “It is not raining and it is pleasant, and it is not pleasant only if it is raining and it is cold” is represented by
(A) (¬p ⋀ r) ⋀ (¬r→p ⋀ q))
(B) (¬p ⋀ r) ⋀ ((p ⋀ q)→¬r )
(C) (¬p ⋀ r) ⋀ ((p ⋀ q)→¬r )
(D) (¬p ⋀ r ) ⋀ (r→(p ⋀ q))
Ans: (A)
7. The Breadth First Search (BFS) algorithm has been implemented using the queue data structure. Which one of the following is a possible order of visiting the nodes in the graph below?
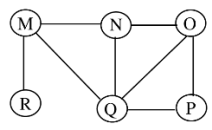
(A) MNOPQR
(B) NQMPOR
(C) QMNROP
(D) POQNMR
Ans: (D)
8. Let 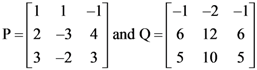 be two matrices.
be two matrices.
Then the rank of P + Q is _________.
Ans: (2)
9. Consider socket API on a Linux machine that supports connected UDP sockets. A connected UDP socket is a UDP socket on which connect function has already been called. Which of the following statements is/are CORRECT ?
I. A connected UDP socket can be used to communicate with multiple peers simultaneously.
II. A process can successfully call connect function again for an already connected UDP socket.
(A) I only
(B) II only
(C) Both I and II
(D) Neither I nor IIs
Ans: (B)
10. The minimum possible number of states of a deterministic automaton that accepts the regular language
L = {w1aw2|w1, w2 ∈ {a, b}*, |w1| = 2,|w2| ≥ 3} is ______.
Ans: (8)
11. Consider the following tables T1 and T2.
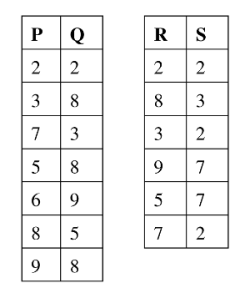
In table T1, P is the primary key and Q is the foreign key referencing R in table T2 with on delete cascade and on-update cascade. In table T2, R is the primary key and S is the foreign key referencing P in table T1 on-delete set NULL and on-update cascade. In order to delete record from table T1, the number of additional records that need to be deleted from table T1 is ______________.
Ans: (0)
12. Which of the following is/are shared by all the threads in a process ?
I. Program counter II. Stack
III. Address space IV. Registers
(A) I and II only
(B) III only
(C) IV only
(D) III and IV only
Ans: (B)
13. A circular queue has been implemented using a single linked list where each node consists of a value and a single pointer pointing to the next node. We maintain exactly two external pointers FRONT and REAR pointing to the front node and the rear node of the queue, respectively. Which of the following statements is/are CORRECT for such a circular queue, so that insertion and deletion operation can be performed in O (1) time ?
I. Next pointer of front node points to the rear node.
II. Next pointer of rear node points to the front node.
(A) I only
(B) II only
(C) Both I and II
(D) Neither I nor II
Ans: (B)
14. Given the following binary number in 32-bit (single precision) IEEE-754 format:
00111110011011010000000000000000
The decimal value closest to this floating- point number is
(A) 1.45 × 101
(B) 1.45 × 10−1
(C) 2.27 × 10−1
(D) 2.27 × 101
Ans: (C)
15. An ER model of a database consists of entity types A and B. These are connected by a relationship R which does not have its own attribute. Under which one of the following conditions, can the relational table for R be merged with that of A?
(A) Relationship R is one-to-many and the participation of A in R is total
(B) Relationship R is one-to-many and the participation of A in R is partial
(C) Relationship R is many-to one and the participation of A in R is total
(D) Relationship R is many-to one and the participation of A in R is partial
Ans: (C)
16. Match the algorithms with their time complexities:
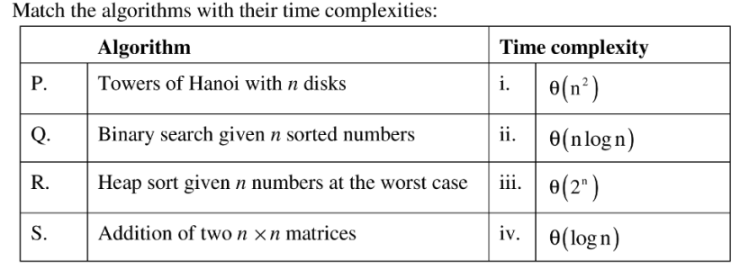
(A) P-(iii),Q-(iv), R-(i), S-(ii)
(B) P-(iv),Q-(iii), R-(i), S-(ii)
(C) P-(iii),Q-(iv), R-(ii), S-(i)
(D) P-(iv),Q-(iii), R-(ii), S-(i)
Ans: (C)
17. Match the following according to input (from the left column) to the complier phase (in the right column) that processes it.
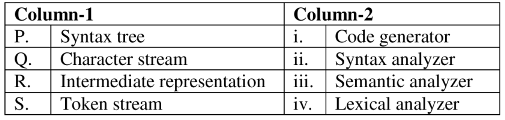
(A) P-(ii),Q-(iii), R-(iv), S-(i)
(B) P-(ii),Q-(i), R-(iii), S-(iv)
(C) P-(iii),Q-(iv), R-(i), S-(ii)
(D) P-(i),Q-(iv), R-(ii), S-(iii)
Ans: (C)
18. Consider the following statements about the routing protocols, Routing Information Protocol (RIP) and Open Shortest Path First (OSPF) in an IPv4 network.
I. RIP uses distance vector routing
II. RIP packets are sent using UDP
III. OSPF packets are sent using TCP
IV. OSPF operation is based on link-state routing
Which of the statements above are CORRECT?
(A) I and IV only
(B) I, II and III only
(C) I, II and IV only
(D) II, III and IV only
Ans: (C)
19. If ![]() and
and ![]() then the constants R and S are respectively
then the constants R and S are respectively
(A) ![]()
(B) ![]()
(C) ![]()
(D) ![]()
Ans: (C)
20. In a file allocation system, which of the following allocation schemes(s) can be used if no external fragmentation is allowed?
I. Contiguous II. Linked III. Indexed
(A) I and III only
(B) II only
(C) III only
(D) II and III only
Ans: (D)
21. Consider a quadratic equation x2 – 13x + 36 = 0 with coefficients in a base b. The solutions of this equation in the same base b are x = 5 and x = 6. Then b = ___________.
Ans: (8)
22. Identify the language generated by the following grammar, where S is start variable.
S → XY
X → aX|a
Y → aYb|∈
(A) {ambn| m ≥ n, n > 0}
(B) {ambn|m ≥ n, n ≥ 0}
(C) {ambn|m > n, n ≥ 0}
(D) {ambn|m > n, n > 0}
Ans: (C)
23. The representation of the value of a 16-bit unsigned integer X in hexadecimal number system is BCA9. The representation of the value of X in octal number system is
(A) 571244
(B) 736251
(C) 571247
(D) 136251
Ans: (D)
24. Consider the following function implemented in C:
void printxy (int x, int y) {
int *ptr ;
x = 0;
ptr = &x;
y = * ptr;
* ptr = l;
print f (“%d, %d,” x, y);
}
The output of invoking printxy (l, l) is
(A) 0, 0
(B) 0, 1
(C) 1, 0
(D) 1, 1
Ans: (C)
25. The maximum number of IPv4 router addresses that can be listed in the record route (RR) option field of an IPv4 header is _________.
Ans: (9)
26. Consider a binary code that consists of only four valid code words as given below:
00000,01011,10101,11110
Let the minimum Hamming distance of the code be p and the maximum number of erroneous bits that can be corrected by the code be q. Then the values of p and q are
(A) p = 3 and q = 1
(B) p = 3 and q = 2
(C) p = 4 and q = 1
(D) p = 4 and q = 2
Ans: (A)
27. A system shares 9 tape drives. The current allocation and maximum requirement of tape drives for three processes are shown below:
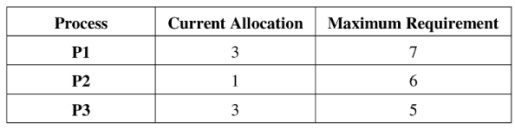
Which of the following best describes current state of the system ?
(A) Safe, Deadlocked
(B) Safe, Not Deadlocked
(C) Not Safe, Deadlocked
(D) Not Safe, Not deadlocked
Ans: (B)
28. Two transactions T1 and T2 are given as
T1 : r1 (X) w1 (X) r1 (Y) w1 (Y)
T2 : r2 (Y) w2 (Y) r2 (Z) w2 (Z)
where ri(V) denotes a read operation by transaction Ti on a variable V and wi(V) denotes a write operations by transaction Ti on a variable V. The total number of conflict serializable schedules that can be formed by T1 and T2 is _____________.
Ans: (54)
29. If w, x, y, z are Boolean variables, then which one of the following is INCORRECT ?
(A) wx +w(x + y) + x(x + y)=x + wy
(B) ![]()
(C) ![]()
(D) (w + y)(wxy + wyz) = wxy + wyz
Ans: (C)
30. Consider the following C Program.
# include <stdio.h>
#include< string.h>
#int main ( ) {
char* c = “GATECSIT2017”;
char* p = c;
printf(“%d”, (int) strlen (c+2[p]-6[p]-1));
return 0;
}
The output of the program is _______________.
Ans: (2)
31. P and Q are considering to apply for a job. The probability that P applies for the job is ![]() The probability that P applies for the job given that Q applies for the job is
The probability that P applies for the job given that Q applies for the job is ![]() and the probability that Q applies for the job given that P applies for the job
and the probability that Q applies for the job given that P applies for the job ![]() Then the probability that P does not apply for the job given that Q does not apply for the job is
Then the probability that P does not apply for the job given that Q does not apply for the job is
(A) ![]()
(B) ![]()
(C) ![]()
(D) ![]()
Ans: (A)
32. If the characteristics polynomial of 3× 3 matrix M over R ( the set of real numbers) is λ3 – 4λ2 + aλ + 30, a ∈ R, and one eigenvalue of M is 2, then the largest among the absolute values of the eigenvalues of M is ________.
Ans: (5)
33. Consider the following expression grammar G:
E → E – T|T
T → T + F|F
F → (E) |id
Which of the following grammars is not left recursive, but is equivalent to G?
(A) 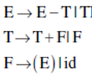
(B) 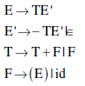
(C) 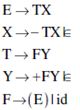
(D) 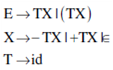
Ans: (C)
34. In a two-level cache system, the access times of L1 and L2 caches are 1 and 8 clock cycles, respectively. The miss penalty from L2 cache to main memory is 18 clock cycles . The miss rate of L1 cache is twice that of L2. The average memory access time (AMAT) of this cache system is 2 cycles. This miss rates of L1 and L2 respectively are :
(A) 0.111 and 0.056
(B) 0.056 and 0.111
(C) 0.0892 and 0.1784
(D) 0.1784 and 0.0892
Ans: (A)
35. Consider two hosts X and Y, connected by a single direct link of rate 106 bits/sec. The distance between the two hosts is 10,000 km and the propagation speed along the link is 2 × 108 m/sec. Host X sends a file of 50,000 bytes as one large message to host Y continuously. Let the transmission and propagation delays be p milliseconds and q milliseconds, respectively . Then the values of p and q are
(A) p = 50 and q = 100
(B) p = 50 and q = 400
(C) p = 100 and q = 50
(D) p = 400 and q = 50
Ans: (D)
36. Consider the recurrence function
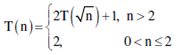
Then T(n) in terms of θ notation is
(A) θ(log log n)
(B) θ(log n)
(C) θ(√n)
(D) θ(n)
Ans: (B)
37. If a random variable X has a Poisson distribution with mean 5, then the expectation E[(X+2)2] equals ______.
Ans: (54)
38. Consider the following C function
int fun (int n) {
int i, j;
for (i = 1; i < = n; i++) {
for (j = 1 ; j < n ; j+=i) {
printf (“%d %d , i, j ) ;
}
}
}
Time complexity of fun in terms of θ notation is
(A) θ(n√n)
(B) θ(n2)
(C) θ(n log n)
(D) θ (n2 log n)
Ans: (C)
39. The pre-order transversal of a binary search tree is given by 12, 8, 6, 2, 7, 9, 10, 16, 15, 19, 17, 20. Then the post-order traversal of this tree is:
(A) 2,6,7,8,9,10,12,15,16,17,19,20
(B) 2,7,6,10,9,8,15,17,20,19,16,12
(C) 7,2,6,8,9,10,20,17,19,15,16,12
(D) 7,6,2,10,9,8,15,16,17,20,19,12
Ans: (B)
40. Consider the C program fragment below which is meant to divide x by y using repeated subtractions. The variables x, y, q and r are all unsigned int.
while (r >= y) {
r = r – y;
q = q +1;
}
Which of the following conditions on the variables x, y, q and r before the execution of the fragment will ensure that the loop terminates in a state satisfying the condition x = = (y*q + r)?
(A) (q = = r) && (r = =0)
(B) (x > 0) && (r = =x) && (y > 0)
(C) (q = = 0) && (r = = x) && (y > 0)
(D) (q = = 0) && (y > 0)
Ans: (C)
41. A message is made up entirely of characters from the set X= {P,Q,R,S,T}. The table of probabilities for each of the characters is shown below:
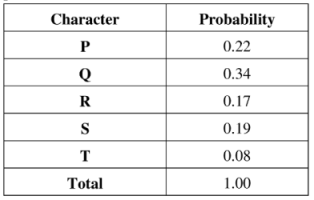
If a message of 100 characters over X is encoded using Huffman coding, then the expected length of the encoded message in bits is_____
Ans: (225)
42. The next state table of a 2-bit saturating up-counter is given below.
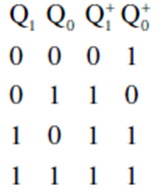
The counter is built as a synchronous sequential circuit using T flip-flops. The expression for T1 and T0 are
(A) ![]()
(B) ![]()
(C) ![]()
(D) ![]()
Ans: (B)
43. Consider the set of processes with arrival time (in milliseconds). CPU burst time (in milliseconds), and priority (0 is the highest priority) shown below. None of the processes have I/O burst time.
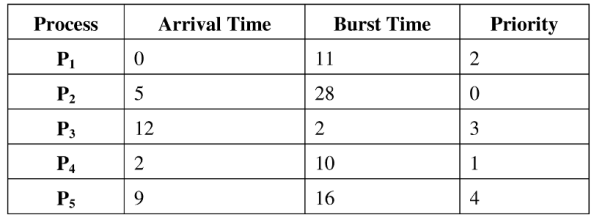
The average waiting time (in milliseconds) of all the processes using preemptive priority scheduling algorithm is __________
Ans: (29)
44. For any discrete random variable X, with probability mass function P(X = j) = pj, pj ≥ 0, j ∈ {0,….. N} and 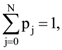 define the polynomial function gx
define the polynomial function gx 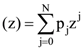 For a certain discrete random variable Y, there exists a scalar β ∈ [0, 1] such that gY (z) = (1 – β+ βz)n. The expectation of Y is
For a certain discrete random variable Y, there exists a scalar β ∈ [0, 1] such that gY (z) = (1 – β+ βz)n. The expectation of Y is
(A) Nβ(1 – β)
(B) Nβ
(C) N(1 – β)
(D) Not expressible in terms of N and β alone
Ans: (B)
45. The read access times and the hit ratios for different caches in a memory hierarchy are as given below.
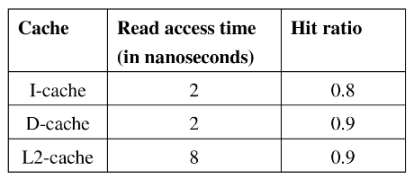
The read access time of main memory is 90 nanoseconds. Assume that the caches use the referred word-first read policy and the write back policy. Assume that all the caches are direct mapped caches. Assume that the dirty bit is always 0 for all the blocks in the caches. In execution of a program, 60% of memory reads are for instruction fetch and 40% are for memory operand fetch. The average read access time in nanoseconds (up to 2 decimal places) is______.
Ans: (4.72)
46. If the ordinary generating function of a sequence 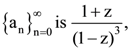 then a3 – a0 is equal to ______.
then a3 – a0 is equal to ______.
Ans: (15)
47. Consider the following snippet of a C program. Assume that swap (&x, &y) exchanges the contents of x and y.
int main ( ) {
int array[]={3,5,1,4,6,2};
int done =0 ;
int i ;
while (done = = 0) {
done = 1;
for (i = 0; i <=4; i ++) {
if (array [i] < array [i +1]) {
swap (& array [i], &array [i+1]);
done = 0;
}
}
for (i = 5 ; i > =1; i –) {
if (array [i] > array [ i-1]) {
swap ( & array [i] , &array [i-1]);
done = 0;
}
}
}
printf ( “ %d “ , array [3] );
}
The output of the program is ____________.
Ans: (3)
48. Consider the following C program.
# include <stdio.h>
int main ( ) {
int m = 10;
int n, n1;
n = ++m;
n1 = m++;
n–;
–n1;
n – = nl;
printf (“%d”, n) ;
return 0;
}
The output of the program is ______________.
Ans: (0)
49. Consider the following database table named top _scorer.
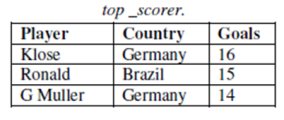
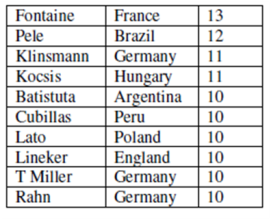
Consider the following SQL query:
SELECT ta.player FROM top _scorer AS ta
WHERE ta.goals > ALL (SELECT tb. goals
FROM top _ scorer AS tb
WHERE tb.country = ‘Spain’)
AND ta.goals > ANY (SELECT tc. goals
FROM top_ scorer AS tc
WHERE tc.country = ‘Germany’)
The number of tuples returned by the above SQL query is ___________.
Ans: (7)
50. Given f (w, x, y, z) = ∑m (0,1,2,3,7,8,10) + ∑d (5,6,11,15), where d represents the don’t care condition in Karnaugh maps. Which of the following is a minimum product-of-sums (POS) form of f(w, x, y, z) ?
(A) ![]()
(B) 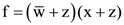
(C) ![]()
(D) ![]()
Ans: (A)
51. In a B+ tree, if the search –key value is 8 bytes long, the block size is 512 bytes and the block pointer size is 2 bytes, then maximum order of the B+ tree is _______________.
Ans: (52)
52. Let L(R) be the language represented by regular expression R. Let L(G) be the language generated by a context free grammar G. Let L (M) be the language accepted by a Turning machine M. Which of the following decision problems are undecidable ?
I. Given a regular expression R and a string w, is w ∈ L(R)?
II. Given a context-free grammar G, L(G) = ∅
III. Given a context-free grammar G, is L(G) = ∑* for some alphabet ∑?
IV. Given a Turning machine M and a string w, is w ∈ L(M)?
(A) I and IV only
(B) II and III only
(C) II, III and IV only
(D) III and IV only
Ans: (D)
53. Consider a machine with a byte addressable main memory of 232bytes divided into blocks of size 32 bytes. Assume that a direct mapped cache having 512 cache lines is used with this machine. The size of the tag field in bits is ______.
Ans: (18)
54. Let δ denote that transition function and denote the extended transition function of the ∈ − NFA whose transition table is given below:
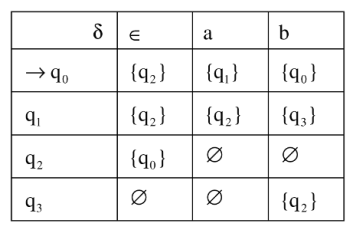
Then ![]() (q2, aba) is
(q2, aba) is
(A) ∅
(B) {q0, q1, q3}
(C) {q0, q1, q2}
(D) {q0, q2, q3}
Ans: (C)
55. Consider the following languages.
L1 = {ap|p is a prime number}
L2 = {anbmc2m|n ≥ 0, m ≥ 0}
L3 = {anbnc2n|n ≥ 0}
L4 = {anbn|n ≥ 1}
Which of the following are CORRECT ?
I. L1 is context-free but not regular.
II. L2 is not context-free.
III. L3 is not context-free but recursive.
IV. L4 is deterministic context-free.
(A) I ,II and IV only
(B) II and III only
(C) I and IV only
(D) III and IV only
Ans: (D)
56. There are 3 red socks, 4 green socks and 3 blue socks, you choose 2 socks. The probability that they are of the same colour is ___________.
(A) 1/5
(B) 7/30
(C) 1/4
(D) 4/15
Ans: (D)
57. Choose the option with words that are not synonyms.
(A) aversion, dislike
(B) luminous, radiant
(C) plunder, loot
(D) yielding, resistant
Ans: (D)
58. There are five buildings called V, W, X, Y and Z in a row (not necessarily in that order). V is to the west of W. Z is to the East of X and the West of V. W is to the West of Y. Which is the building in the middle ?
(A) V
(B) W
(C) X
(D) Y
Ans: (A)
59. A test has twenty questions worth 100 marks in total. There are two types of questions, multiple choice questions are worth 3 marks each and essay questions are worth 11 marks each. How many multiple choice questions does the exam have?
(A) 12
(B) 15
(C) 18
(D) 19
Ans: (B)
60. Saturn is ____ to be seen on a clear night with the naked eye.
(A) enough bright
(B) bright enough
(C) as enough bright
(D) bright as enough
Ans: (B)
61. “We lived in a culture that denied any merit to literary works, considering them important only when they were handmaidens to something seemingly more urgent – namely ideology. This was a country where all gestures, even the most private, were interpreted in political terms.”
The author’s belief that ideology is not as important as literature is revealed by the word:
(A) ‘culture’
(B) ‘seemingly’
(C) ‘urgent’
(D) ‘political’
Ans: (B)
62. X is a 30 digit number starting with the digit 4 followed by the digit 7, then the number X3 will have
(A) 90 digits
(B) 91 digits
(C) 92 digits
(D) 93 digits
Ans: (A)
63. There are three boxes, one contains apples, another contains oranges and the last one contains both apples and oranges. All three are known to be incorrectly labelled. If you are permitted to open just one box and then pull out and inspect only one fruit, which box would you open to determine the contents of all three boxes?
(A) The box labelled ‘Apples’
(B) The box labelled ‘Apples and Oranges’
(C) The box labelled ‘Oranges’
(D) Cannot be determined
Ans: (B)
64. An air pressure contour line joins locations in a region having the same atmospheric pressure . The following is an air contour plot of a geographical region . Contour lines are shown at 0.05 bar intervals in this plot.
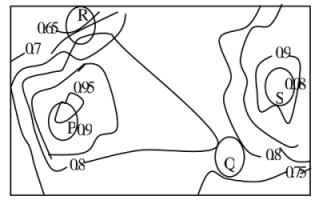
If the possibility of a thunderstorm is given by how fast air pressure rises or drops over a region, which of the following regions is most likely to have a thunderstorm?
(A) P
(B) Q
(C) R
(D) S
Ans: (C)
65. The number of roots of ex + 0.5x2 – 2 = 0 in the range [−5, 5] is
(A) 0
(B) 1
(C) 2
(D) 3
Ans: (A)
Latest Govt Job & Exam Updates: